TTPs
A bit ago, I ran across this fascinating blog post regarding the
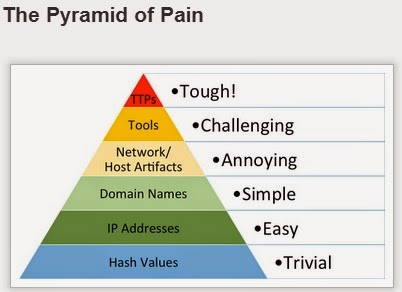
Pyramid of Pain. Yes, it's over a year old, but it's still relevant today.
For one thing, back when I was doing PCI exams (while a member of the IBM ISS ERS team), Visa would send us these lists which included file names (no paths) and hashes...we had to search for them in every exam, so we did. While I could see the value in the searches themselves, I felt at the time that Visa was sitting on a great deal of valuable intelligence that, if shared and used properly, could not only help us with our analysis, but could also be used to
protect the victim merchants. After all, if we knew more about how the bad guys were getting in and how they were targeting specific systems (TTPs), we could help prevent and detect such things. As such, it was validating to see someone else discuss the value of such things.
Over the years, I've heard others talk about things like attribution, when it came to "APT" (I apologize for using that term...). In fact, at one conference in particular, the speaker talked about how examples of code could be used for attribution, but shortly thereafter stated that the code could be downloaded from the Internet, and that various snippets could be pasted together to form working malware.
Indicators
In his recent RSA Confernce
State of the Hack talk, Kevin Mandia said that in the APT1 report, 3000 indicators were released...he mentioned domains and IP addresses, specifically. Those are pretty low on the pyramid.
I have to agree that tools don't make the threat group, as many seem to be using the same tools. In fact, it seems that a lot of the tools used for infrastructure recon are native tools...so which group gets the attribution? Microsoft? ;-)
Every time I read over the blog post, I keep coming back to agreeing with what the author says about TTPs. Once you're to the point of detecting behaviors, you're no longer concerned with things like disclosure (public or otherwise) resulting in an adversary changing/adapting their tactics...because now, rather than focusing on individual data points, you have a process in place. In particular, that process is iterative...anything new you learn gets rolled right back into the process and shared amongst all responders, thereby improving the overall response process. What you want to do is get to the point where you stop reacting to the adversary, and instead, they react to you.
RegRipper EnScript
I recently found out that
someone is selling an EnScript to tie RegRipper into EnCase. Some tweeted questions about how I felt about it, if I was receiving royalties, and asking if it "violated the GPL"...which, honestly, I didn't understand, as the license file in the archive specifies the license. Why ask me if the answer is right there?
Since Twitter really isn't the medium for this sort of thing (and I honestly have no idea why so many people in the DFIR community restrict themselves to that medium), I thought I'd share my thoughts here. First, others are making money off of free software, in general, and a few are doing so specifically with RegRipper...so why is this particular situation any different? The
GPL v3 quick guide states, in part, that users should have the freedom to "use the software for any purpose". It further goes on to state that free software should remain free...and in this case, it would appear that RR remains free, and the $15 pays for the EnScript. As such, I'm wouldn't think that selling the EnScript violates anything.
Second, this is clearly an attempt to bring the use of RR to users of EnCase. I've never been a big fan of EnCase, but I realize that there are a number of folks who are, and that many specifically rely on this software. My original purpose for releasing RegRipper was to put it out in the community for others to use and improve upon...well, that second part really hasn't happened to a great extent, and I don't see this EnScript either taking anything away from RegRipper, or adding anything to it.
RegRipper
I'm not saying that no one has offered up ways for improving RegRipper...some have. Not long ago, I received a plugin from someone, and Corey Harrell submitted one just the other day. I've had exchanges recently with some folks who have had some thoughtful suggestions regarding how to improve RegRipper, and perhaps make it more useful to a wider range of users. All I'm saying is that it hasn't happened to a great extent; some of the improvements and updates (
inclusion of alerts,
RLO plugin, etc.) are things I've added for my own benefit, and I don't want to maintain two disparate source trees.
Does this mean that more people are likely to use it? Hhhhhmmmm...maybe. Folks who go this route are likely going to go the same route as most of the folks who already use RegRipper, either by downloading it or using it as part of a consolidated distribution. That is to say, they're just going to just blindly run all plugins against the hives that they have available, and it's unlikely that there're going to have any ideas for new plugins (or tool updates or improvements as a whole) coming from this crowd.
So, in short, I don't see how this EnScript is a violation of anything...it's no different from what others are doing, and RegRipper itself remains free. Further, it takes nothing away from RegRipper, nor adds anything to it.
Finally, Jamie had a good point on Twitter...if you don't want this to happen, don't put stuff out there for free. Point well taken.
Speaking of which, I had an email exchange with Jamie and Corey Harrell recently, where we discussed some well-considered possible future additions to RegRipper.
Book
Windows Forensic Analysis 4/e is due to be released soon...I need to complete the archive of materials that go along with the book and get it posted. As soon as that's done, I will start working on the possible additions to RegRipper.
Malware Detection
Speaking of
WFA 4/e, one of the chapters I kept was the one on
Malware Detection. Not long ago, I was following the steps that I had laid out in that chapter, and I found that the system had McAfee AV installed. So, per my process, I noted this to (a) be sure that I didn't run the same product against the image (mounted as read-only volume) and (b) look for logs and quarantined items.
It turns out that when McAfee AV quarantines an item, it creates a .bup file, which follows the MS CFB file format.
This Open Security Research blog post is very helpful in opening the files up, in part because it points to
this McAfee Knowledge Center article on the same topic.
Some additional resources:
Punbup - Python script for parsing BUP files
Bup-parse - Enscript for parsing BUP files
McBup - Another Python script that may be useful
Conferences
I'll be speaking at a couple of conferences here in the near future. I'm giving two presentations at the
USACyberCrime Conference (formerly known as the DoD CyberCrime Conference, or DC3) at the end of April. My presentations will be "
APT sans Malware", and "
Registry Analysis". It's unlikely that I will be posting the PPTXs for these, as I'm not putting everything I'm going to say in bullets in the slides...if I did, what would be the point of me actually speaking, right?
Thanks to
Suzanne Widup, I'll be speaking on the author's panel at the
SANS Forensics Summit in Austin, TX, in June. This is something new, and something I'm looking forward to. Not getting feedback from the community regarding what they'd like to see or hear in a presentation, I've backed away somewhat from submitting presentations to CfPs that are posted. One of my go-to presentations is
Registry Analysis, in part because I really believe that it's a critical component of Windows forensic analysis, and also because I'm not sure that analysts are doing it correctly. However, I've been told that I need to present on something else...but not what. Also, the panel format is more free-form...I was on a panel at one of the first SANS Forensic Summits, and if you've attended any of the Open Memory Forensic Workshops, you've seen how interesting a panel can be.
 Brett Shavers has posted the first (that I'm aware of) reviews of WFA 4/e...one on Amazon, and a longer one can be found on his WinFE blog.
Brett Shavers has posted the first (that I'm aware of) reviews of WFA 4/e...one on Amazon, and a longer one can be found on his WinFE blog.