With respect to USB devices in particular, not long ago, we (the community) became aware that the Microsoft-Windows-DriverFrameworks-UserMode/Operational Event Log contained quite a bit of information (see this post for event IDs to track) that a digital forensic analyst could use to determine if and when USB devices had been connected to (and disconnected from) the system. This was a pretty profound finding, and very valuable...and then, for some unknown reason, that Windows Event Log was disabled by default.
Also, in researching information for this topic, I found that the EMDMgmt key in the Software hive, which is associated with ReadyBoost and provided insight into USB-connected devices, is no longer available either. Okay, so one less artifact, one artifact removed from the constellation...now we just need to adapt.
This is really nothing new, to be honest. DFIR analysts need to be adaptable, regardless of whether we're in a consultant or FTE role. If you're a consultant, you're going to see a new environment on every engagement, and there will be new things to deal with and discover. A while back, a teammate discovered that the customer had LANDesk installed on their systems, and the software monitoring component recorded a great deal of information regarding executed processes right there in the Registry. It's not too different in an internal, FTE role, as you're likely going to run across legacy builds, software loads that haven't been/can't be updated for some reason, applications or packages users have installed specifically to meet the needs of their department or of a customer, etc. Further, we've seen various resources come and go; for example, we got used to having Registry hive backups available during investigations, and then we lost access to them; they're no longer available by default. In addition to the Microsoft-Windows-DriverFrameworks-UserMode/Operational Event Log, the Microsoft-Windows-TaskScheduler/Operational Event Log seems to be disabled by default. As such, when we find that a data source or artifact that we're familiar with and used to using is no longer available, we have to invest in determining an alternate means for determining the same or similar information; we have to rebuild those artifact constellations.
Something else that has developed over time alongside the development of the Windows platform is how USB devices are treated. For example, Nicole Ibrahim described some time ago how some USB connected devices, specifically smartphones, are treated differently based on the protocol used. Nicole's presentation on the topic can be found here.
The overall point is that we can no longer consider all USB-connected devices to be the same, and as such, we may need to look in different locations within the OS, including different locations within the Registry and within different Windows Event Logs, to find the information pursuant to our analysis goals. Pursuant to this, I sat down with my own local system and started going through the Windows Event Logs, via the Event Viewer, one at a time, looking for indications of connected devices. What I found was that records of connections were dispersed across multiple logs, depending upon the type of device connected (i.e., smartphone/digital camera, ext HDD w/ enclosure, thumb drive, etc.).
As a caveat, these event records are not exclusive; that is to say that the individual event source/ID pairs do not pertain solely to USB connected devices. In many cases, the same event source/ID pair was found to contain information specific to the local physical hard drive, as well as to the different volumes on that hard drive. Also, all of these events are for the latest build of Windows 10 only, because that's all I have to test against.
So here's a look at the five resources I found; keep in mind this is limited based on what I have available to test with, but it should serve as a good starting point...
Microsoft-Windows-WPD-MTPClassDriver/Operational.evtx
Event Source: WPD-MTPClassDriver
Event ID: 1005
 |
| Fig 1: Event ID 1005 |
Figure 1 illustrates where I'd connected my iPhone to the system to pull pictures; I also have entries for my iPod (yes, I still have an iPod...) where I wanted to transfer music to my iPhone. Due to the protocol used, this is also where we'd likely find digital cameras, as well.
Microsoft-Windows-DeviceSetupManager/Admin
Event Source: DeviceSetupManager
Event ID: 112
 |
| Fig 2: Event ID 112 |
Figure 2 shows where I'd connected a SanDisk Cruzer thumb drive to the computer.
Microsoft-Windows-StorageSpaces-Driver/Operational.evtx
Event Source: StorageSpaces-Driver
Event ID: 207
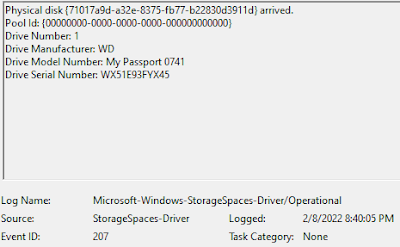 |
| Fig 3: Event ID 207 |
I shared figure 3 because this is specifically an external HDD, one of those "wallet" drives with a small form factor/enclosure. This device is small enough that it's powered from the USB connection; I don't have a larger enclosure that requires an additional power source to test against.
Microsoft-Windows-Partition/Diagnostic.evtx
Event Source: Partition
Event ID: 1006
 |
| Fig 4: Event ID 1006, XML view |
Figure 4 is a bit different, because the "friendly view" simply says, "for internal use only". However, taking a look at the XML view, we see that the SanDisk Cruzer thumb drive and it's serial number pops right out!
Microsoft-Windows-Ntfs/Operational.evtx
Event Source: Ntfs
Event ID: 145, 142
 |
| Fig 5: Event ID 145 |
Figure 5 shows the Ntfs/145 event record (in part) from a previous connection of the SanDisk Cruzer thumb drive. Event ID 142 provides additional information, including regarding the volume assignment (C:, D:, F:, etc.), if the volume is bootable, etc., which can be used to tie to shellbags and Windows Portable Devices artifacts in the Registry.
Recommendations
From a forensic perspective, if you're interested in tracking USB devices connected to systems, I'd recommend enabling the Microsoft-Windows-DriverFrameworks-UserMode/Operational Event Log, forwarding those event records off of the system (for processing via a SIEM), as well as threat hunting or some other mechanism to ensure that if the log is disabled again that this is detected and responded to in the appropriate manner.
Note that enabling the Microsoft-Windows-DriverFrameworks-UserMode/Operational Event Log is as straightforward as setting the "Enabled" value in the HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\WINEVT\Channels\Microsoft-Windows-DriverFrameworks-UserMode/Operational key to "1" and rebooting the system. As a tip to DFIR analysts who need to perform verification and to threat hunters, the reverse technique (setting the "Enabled" value to "0") can be used disable normally-available Windows Event Logs.
Additional Resources
HEFC Blog - Sunday Funday, Daily Blog #197
HEFC Blog - Sunday Funday, Daily Blog #197
USB Storage Device Forensics for Windows 10, circa 2017
Computer Forensics CCIC Training, chapter 8, circa 2017
This solves most all obstacles:
ReplyDelete"DFIR analysts need to be adaptable"
@Brett,
ReplyDeleteThat comment was based on experience. In my own roles, walking into a new environment means that nothing is what I would assume it would be. One environment runs completely on MS defaults, but the next is highly customized.
The other aspect of this is, never stop learning.
I’d also recommend 39 & 40 in Microsoft-Windows-MBAM/Operational. Never did a write up, just a Tweet. https://twitter.com/bmmaloney97/status/938834644417630208?s=21&t=Cf9MA_48bSzfTWWJUbGSkA
DeleteThanks so much far this helpful post;)
ReplyDelete